Introduction
The Internet of Things (IoT) has transformed how we are involved with technology by enabling seamless connection and automation across multiple fields. But as the number of devices linked to the internet keeps growing, so does the requirement for adequate safety precautions for protecting private information and guaranteeing the stability of IoT ecosystems. In this post, we’ll look at the major developments, obstacles, and trends effect pcb design engineer and are impacting hardware security in Internet of Things devices.
Future of Hardware Security in IoT Devices
- Solutions for Secure Embedded Hardware
Embedded hardware security solutions are set to be essential in securing Internet of Things devices from new and emerging threats. Various hardware-based approaches, such as hardware security modules (HSMs), trusted platform modules (TPMs), and encrypted components, are all present in these systems. Embedded security solutions provide devices a strong base for protecting sensitive data, authenticating devices, and proving tamper resistance by embedding cryptographic capacity effectively within the device’s hardware, for instance, microcontrollers or system-on-chips (SoCs). Furthermore, the creation of customised security measures that are adapted to the unique needs of Internet of Things applications is made feasible by technological improvements in silicon manufacturing, enhancing the security and resilience of devices even further.
- Basis of Reliability and Safe Boot
The key elements of hardware security in Internet of Things devices involve creating a root of trust and putting shielded boot mechanisms in effect. The framework for confirming the genuineness and consistency of the firmware and software elements of the device is a root of trust. Usually, cryptographic keys preserved in safe hardware components—like trusted platform modules or hardware security modules—are used in this process. However, secure boot reduces the possibility of malware filtration and unauthorised code execution by guaranteeing that only verified and unmodified firmware and applications are installed during the device boot process. When paired together, these safety features provide a secure working atmosphere for the gadget, guarding against both external and internal threats.
- Hardware-Supported Cryptography
One of the main factors supporting data security and authentication in Internet of Things devices is hardware-based cryptography. Hardware-based cryptography help hardware designer optimises speed, efficiency, and durability against side-channel breaches by shifting cryptographic processes to specialised hardware acceleration devices, like cryptographic shared processors or accelerators built into the device’s SoC. Furthermore, a variety of cryptographic techniques, including electronic signatures, symmetric and asymmetric encryption, and key exchange protocols, can be processed by hardware-based cryptographic engines, enabling strong data privacy and authentication methods for Internet of Things applications. IoT security designs will continue to rely extensively on hardware-based encryption as the need for secure interaction and information confidentiality grows.
- Implementing Practical Security Policies
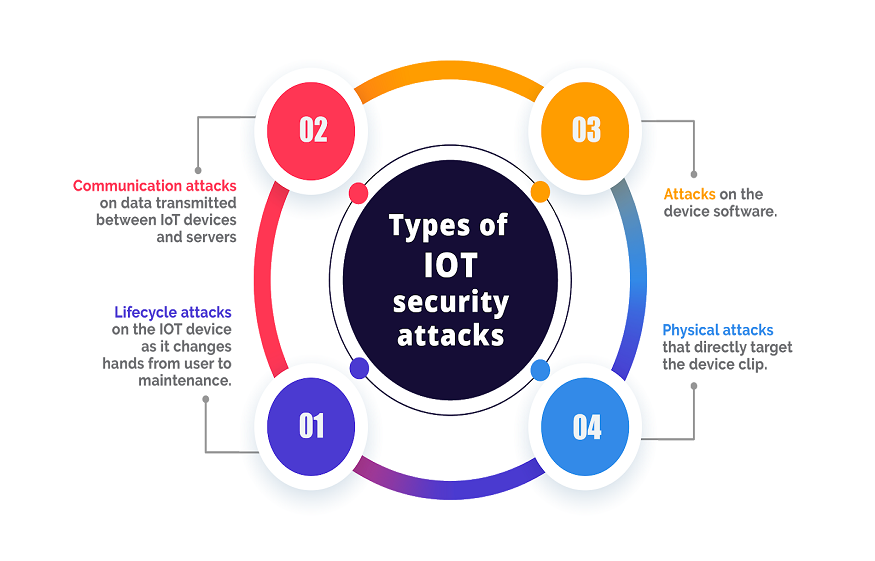
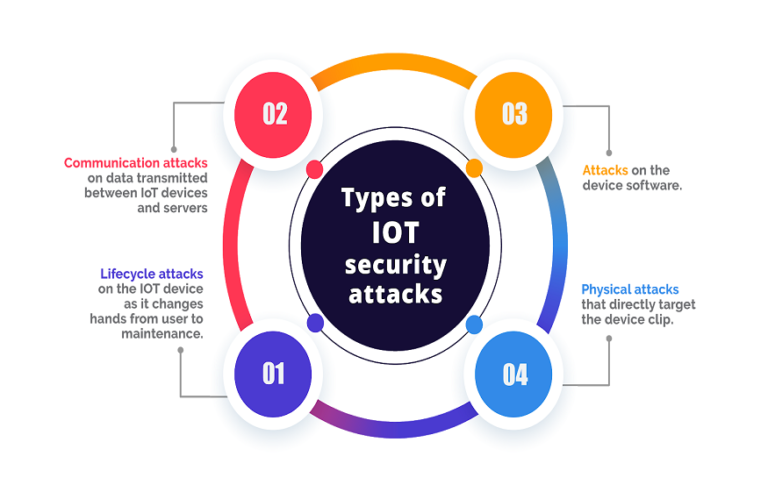
Physical security measures have become essential for preventing unwanted access and tampering with IoT devices alongside cryptographic solutions. Intrusion detection sensors, enclosure seals, tamper-evident packaging, and anti-tamper coatings are a few instances of physical security measures. These security measures warn administrators about prospective breaches and initiate preventative measures like device lockout or data deletion, which assist in avoiding physical assaults like hacking, hardware tampering, and unauthorised device disassembly. Furthermore, security encapsulation and anti-tamper mesh layers—two breakthroughs in tamper-resistant hardware design—are strengthening the ability of IoT devices to endure complex physical assaults, protecting sensitive data’s confidentiality and integrity.
- Lifecycle Management of Devices and Supply Chain Security
To guarantee the overall security and reliability of IoT installations, security of the supply chain and device lifecycle administration are essential factors to take into account. Supply chain collisions, such as firmware supply chain attacks or hardware trojans significantly jeopardise the integrity and security of IoT devices. This emphasises the need to meticulously pick and confirm the suppliers of hardware, firmware, and software. Furthermore, a strong device lifecycle management strategy that includes device decommissioning, over-the-air (OTA) upgrades, and secure provisioning helps to ensure that IoT devices remain safe during their entire existence. Organisations can minimise the risk of supply chain attacks, guarantee prompt security upgrades, and proactively address safety risks in deployed devices by creating secure supply chains and placing complete lifecycle management plans into place.
- New Technologies: Cryptography Secured by Quantum
Traditional cryptography techniques are confronted with a changing danger scenario as quantum computing advances. By making use of their intrinsic flaws in quantum algorithms, like Shor’s algorithm, quantum devices have the ability to compromise popular encryption systems like RSA and ECC. A solution to this problem is the use of quantum-safe cryptography, which depends on cryptographic primitives that are resistant to quantum assaults. Researchers and industry players are investigating this approach. Ensuring the long-term secrecy and integrity of sensitive data in the Internet of Things contexts, quantum-safe cryptographic methods, such as hash-based authentication and lattice-based encryption, provide strong security considerations from quantum attackers. As quantum computing grows, future-proofing IoT security designs and reducing the danger of quantum-based attacks will need the incorporation of quantum-safe encryption techniques into IoT hardware platforms.
- Frameworks for Standardisation and Certification
In order to create industry-wide best practices and guarantee conformity to security rules and regulations, standardisation, and certification frameworks are required. The Internet of Things (IoT) security standards and specifications, which address issues like device authentication, data encryption, and secure communication protocols, are being produced by groups like the Internet Engineering Task Force (IETF), the Trusted Computing Group (TCG), and the International Organisation for Standardisation (ISO). Furthermore, accreditation systems like Common Criteria (CC) and FIPS 140-2 support the development of trust in the security capabilities of IoT devices by offering independent confirmation of security claims. It is possible for IoT device makers to show their dedication to security and interoperability, build consumer confidence, and encourage the adoption of secure IoT solutions by following established standards and acquiring the necessary certifications.
Conclusion
To sum up, hardware security is the foundation of the Internet of Things device security and offers vital defences against a variety of threats, including physical manipulation and remote assaults. Through the use of developing technologies like quantum-safe cryptography, physical safety precautions, cryptographic approaches, and embedded hardware safety options, organisations could improve the dependability and credibility of IoT installations. In addition, complying with certification and standardisation standards in semiconductor design company promotes trust in the safety posture of IoT devices and creates a uniform security baseline. To protect sensitive data, protect user privacy, and ensure the continued viability of IoT applications, it will be crucial to invest in robust physical security mechanisms as IoT ecosystems keep growing.










+ There are no comments
Add yours